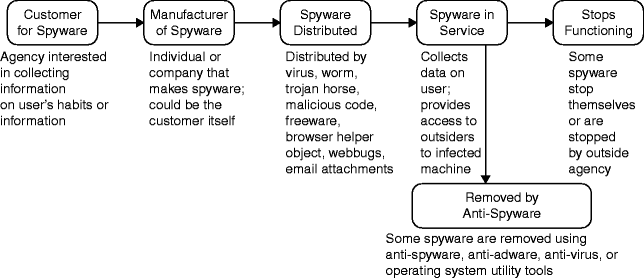
Spyware (spying software) is a term to mark a wide range of computer programs that track user behavior, collect sensitive data, and transfer it somewhere else as their primary purpose or one of the available functions. Some software like modern web browsers, for example, openly and with users’ allowance conducts tracking to improve its performance. Such programs are not considered spyware. Spyware does its work unbeknownst to users, without their consent, and with different consequences.
Spyware automatically sends the collected data to the places whence it can be sold or immediately used against the victim. Many interested parties can use the stolen data to improve ad targeting, hack the injured party’s web accounts, penetrate their systems, blackmail, or racketeer them. The consequences of spyware infections vary. However, even the side effects of these programs’ work determine spyware being most often classified as malware. If spying is only one of the functions of some uninstallable program, that piece of software precisely might be called a potentially unwanted application (PUA) instead of malware. But that is rather an exception.
Types of spyware
Spyware can barely be divided into types. Modern examples of this sophisticated malware contain all things that were more typical for separated malware strains. These days, all these nasty things are present together, under the hood of a single malware sample. So don’t be surprised with seeing things that earlier were listed as a separate malware type.
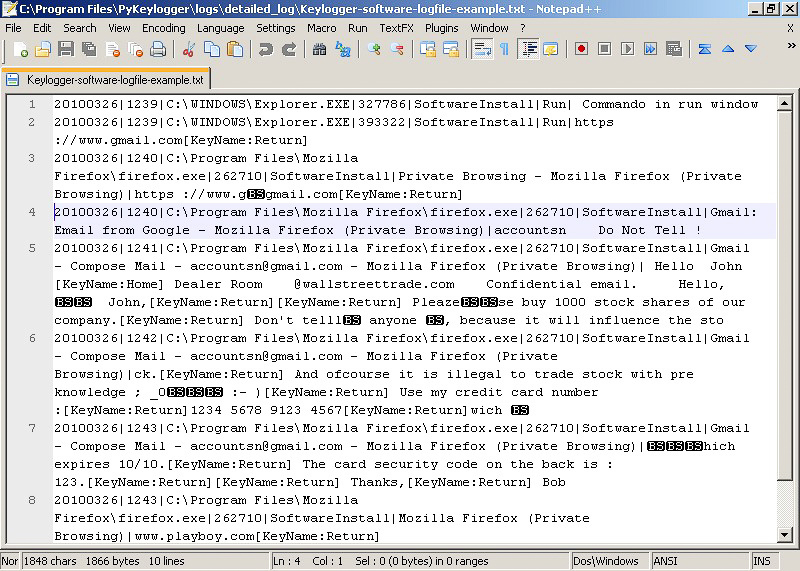
Keyloggers
That malicious thing records each keystroke you do, including the buttons on system unit and mouse. You may think that such function may not be useful these days, but cybercriminals say contrary. With the help of keylogger, crooks may obtain your passwords even if you use secure software that does not keep your passwords in unprotected form. The ability to get this, and various other information from the hardware makes it pretty useful in spying purposes.
Password stealers
As it is clear from the name of this type of spyware, password stealers are targeting passwords and other automatically filled values stored in web browsers. Password stealers can work alongside keyloggers which then allows them to collect passwords ad hoc, right as the user enters them. However, much more often target of this kind of stealers are the programs that store your passwords in an unprotected form. Cybercriminals who design malware know which apps do so, hence, they will not get lost.
Banking Trojans
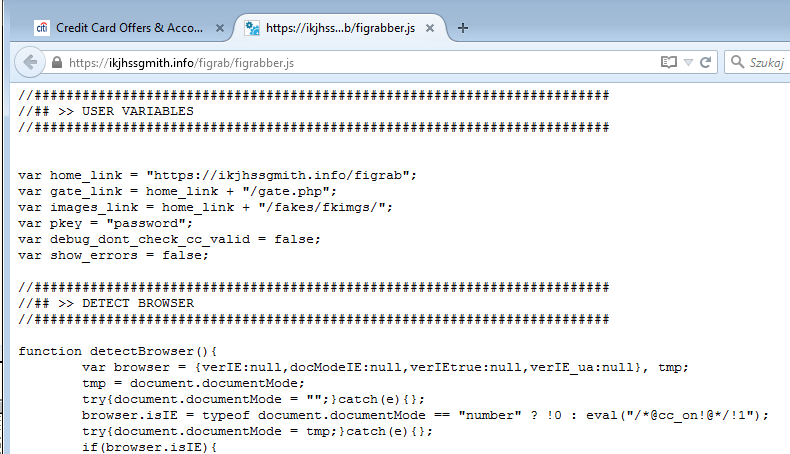
These spying programs have a lot in common with password stealers. The exception is that banking trojans aim specifically at the finance-related credentials of credit cards, bank accounts, and various digital wallets. They are widespread for both desktop and mobile operating systems. Since almost all people who have a bank account manage their stuff from the application or a website, banking trojans may bring a lot of money to cybercriminals.
Info stealers
Info stealers hunt for certain types of data: usernames and passwords, browser history, log files, documents, and media files. Deploying an info stealer is often a part of massive hacker campaigns. This malware type is considered to be the example of a classic stealer malware. They may aim on some file formats, or even look for a certain file on your disk – for example, a valuable report or compromising materials.
Trackers
Analysts sometimes call it “a classic spyware”. Initially, spyware appeared to… spy on the victims. Hackers designed it to gather information about the victims’ location, activity hours, personal information, PC configuration, and so on. Such a program alters your web browser’s settings and collects data that your browser generates and passes through itself. The spyware automatically delivers this data to the offenders who later sell it. In some cases, you can get spyware inside of the other malware – so-called browser hijackers. Spyware within a browser hijacker usually comes along with relatively harmless adware. As soon as adware reveals its presence in a browser, it should be removed because of the concomitant spyware.
Spyware examples
There were hundreds, or even thousands spyware examples. However, only certain things worth your attention. AzorUlt – Trojan-carried spyware usually deployed along with ransomware. It steals finance-related data and might also steal cryptocurrency. Along with the targeted usage, it was also noted as an actor of wide-public attacks with ransomware spreading. However, when we talk about targeted attacks, it is impossible to ignore an Israeli brainchild – the Pegasus spyware. Pegasus is an example of so-called “policeware.” This kind of spyware is developed for governmental needs, but criminals can also use it. Pegasus runs on iOS and Android portable devices where it can be covertly installed. The program can track calls, steal passwords, and spy on messaging.
Vidar – this Trojan, infiltrating via system vulnerabilities, allows criminals to specify the data they want to collect. It can be credit cards numbers or passwords, for example. Vidar can also jeopardize its victims’ digital wallets. It is less widespread than ones I have mentioned above, but is famous for high efficiency.
Harm and threats
Spyware’s evident harm is systems performance degradation and problems with connectivity. Adware infestation is also possible as a collateral factor. However, the real threat is invisible. With the help of spyware, hackers can steal money from the victim’s bank account, withdraw cryptocurrency from the wallet, blackmail, stalk, and racketeer the victim (based on gained sensitive materials.) Finally, they can bring to life the worst scenario that encompasses all the menaces of those already mentioned – identity theft.
How can spyware infect the victim’s PC
Spyware penetrates systems through system vulnerabilities or human inattentiveness. This happens either unbeknownst to users or via overt deception, but often hackers use both tactics at once. For example, Zlob spyware arrives in disguise as an ActiveX codec, but then the user is offered to download a fake anti-spyware program which turns out to be a Trojan-Downloader to bring much more threats to the victim’s PC.
How to protect yourself?
Realize that the Internet is a place where you can encounter fraud and actual harm done to you by malefactors. Make no mistake: just like in the real world – there are safe and unsafe places on the Web. Most hacker attacks rely on the lack of this understanding.
Don’t follow unchecked links or open attachments to strange emails you have never expected to receive. Examine the sender’s address and the body of the letter for typos and mistakes that would expose the deception. Try to contact the sender via other channels before you decide to do anything. The same goes for SMS, chats on social media, and messaging applications.
Install efficient anti-malware software. It will cover most of the human omissions. A good security program will detect and remove any hidden malware after scanning your computer’s drives. It will also protect your system from anything being installed thereon in real-time. Finally, these programs feature Internet browsing protection to block dangerous web pages and warn users about questionable ones.
Ignore web advertising that offers you anything (most likely a computer program) you never searched for and in which you are not a specialist. If you are still interested, consult an expert or at least read users’ feedback on the solution in question.
