A potentially unwanted program, or PUP, is an application that is considered unsafe. In rare cases, the exact app is safe, but there are a lot of alterations that are spread in the Internet and are malicious. Although these programs may carry a real functionality, they can damage your system or your files as well.
What are unwanted programs (PUP/PUA)?
Unwanted programs may have different origins. Some of them are just poorly made, so their usage may lead to file corruption or system failures. Especially dangerous are ones that edit your registry or system files. Another widespread variation of “benevolent-but-unwanted” apps are programs that contain a lot of advertisements – like uTorrent. They can be really useful and not harmful in their main task, but side actions can expose you to malware injection.
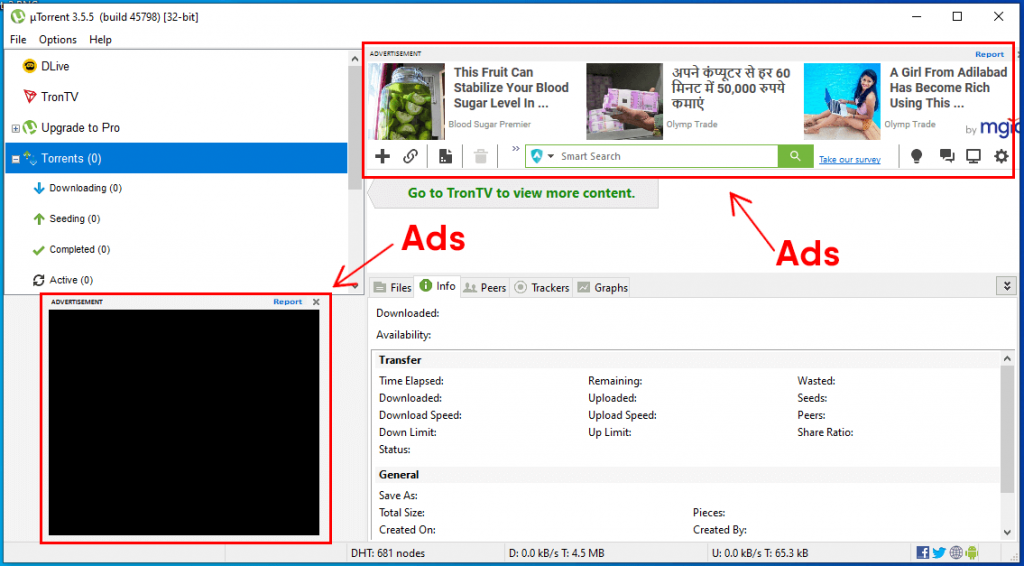
The other class of unwanted programs usually means that even the main functionality is questionable. You can think it is similar to poorly-made ones – and they really are. But the latter are made so they may damage your system unintentionally – because of low skills or so. Meanwhile, questionable tools expose you to the hazards directly and intentionally. Different driver updaters, system optimizers and other things may act as trojan-downloaders.
There are also variants of unwanted programs when they fully represent their naming. Such apps appear on your computer when you don’t expect them. Usually, such programs are getting into your system as a part of a bundle. Such a pack of programs may contain whatever – from full-fledged malware to just such annoying stuff. When it comes while you don’t want it to come – it is definitely not a good case.
PUA examples:
Are unwanted programs dangerous?
Depending on the class of such apps, their danger may vary from just annoying you to heavy corruption of your PC. Most of the unwanted programs cannot expose you to any serious threats, but it is still unpleasant to have some of your system elements malfunctioning. Such tools are registry optimizers, system boosters or some utilities for interface modifying. Even though they may have some useful functionality, the way these functions are realized feels like an elephant in the china shop.
Much more danger goes from so-called driver updaters and pseudo-antiviruses. Such utilities are also classified as rogue: once being created with a legit purpose, they became a source of problems for users. “Driver updaters” are a nightmare because no one can say for sure where they take those drivers. Hence, you may easily get an outdated one, or what is worse – malware instead of driver. Malware which is activated on the driver level can control the whole OS – and be sure, malware developers will never ignore such a chance.
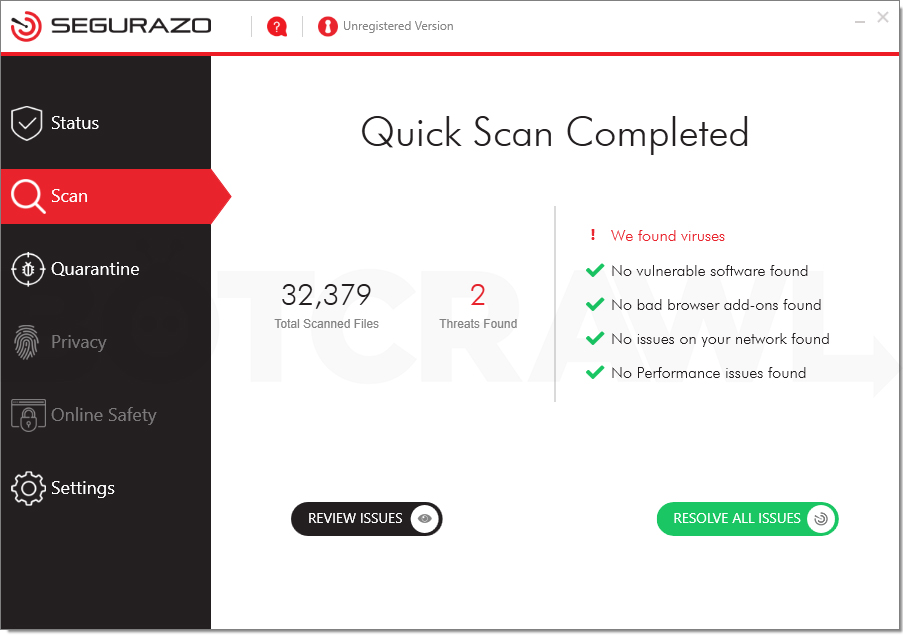
Fake antivirus software is not so dangerous, but makes your PC usage experience as unpleasant as it can even be. They “scan” your computer, and then show you tons of “malware” it has detected. In fact, all detected items are legit – it can mark your Photoshop projects as well as files of other antivirus software. Most of such programs will just distract you with continuous notifications, but the vilest ones will even block the detections. Hence, you may even lose access to some of your programs – just because that “antivirus” decided to block its .exe file.
How to protect your computer from PUP/PUA?
PUAs are pretty easy to avoid. Fortunately, they are not spread in any sophisticated way, so following some basic rules will minimize the chances of being infected. However, since some PUPs are distributed with the use of social engineering, it is important to be aware.
First and the most effective advice is to stop using untrustworthy/unofficial sources of software. Those places are full of hacked programs, and bundles – the most widespread sources of unwanted programs – are the way to monetize the hackers’ work. And they will not likely check the benevolence of programs they are offering in a bundle. When you have no choice instead of using the hacked app, check the installation window attentively for possible installation options.