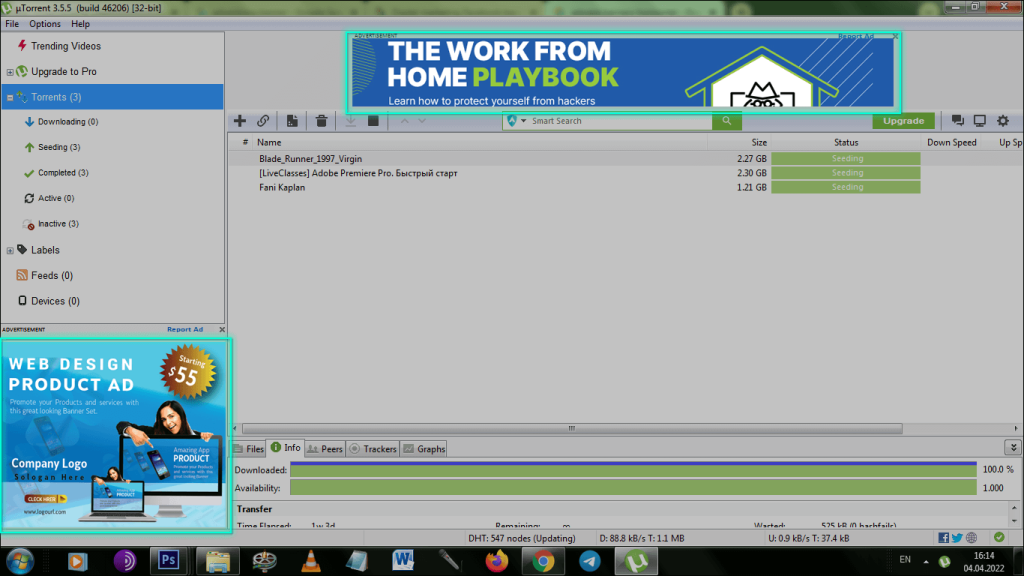
Adware is the name for a vast amount of software that contains advertising. It can be both paid or free, handy or useless, annoying or harmful, but the unifying factor is the presence of advertising within the product.
In the context of Internet security, adware brings frustration and inconvenience to users, sneaks into their devices stealthily or via open deception, and most likely exploits users’ ignorance. Adware refers to various types of desktop and mobile software. Its diversity is as wide as the range of programs adware tries to mimic and present itself as. These can be Internet-related applications of all sorts: web browsers, browser extensions, image editors, messengers, GPS navigators, etc. Uselessness, pseudo-functionality, and intrusive advertising as their true purpose are the common attributes of such apps.
What does adware look like?
Adware is a very flexible and modifiable type of malware. Therefore, you may observe different forms this thing obtains, depending on the severeness and spreading method. The most “classic” adware is more like any other malware type: it runs as a dubious .exe file in your Task Manager and sits somewhere in the AppData\Local\Temp folder. These malware strains are usually the hardest ones. You will likely struggle even to perform a search query – this thing will redirect you from Google to the page with ads or so.
Fortunately, we can conclude that these days such a severe thing is a minor case. More often the situation is an adware module inside of the thing that tries to look like something legit. Torrent-trackers, pseudo-navigators, network settings management tools – they may even carry the declared functionality. But simultaneously, you will see the ads on each page you open. Adware payload in those apps can forcibly open your browser to show you another portion of ads – it will be a very unpleasant experience during a conference of some sort.
Adware classification
Some of the security specialists classify this malware type as potentially unwanted programs (PUPs), not malware. The reason for that is the absence of direct harm coming from adware. Yes, it does parasitize on uneducated users, it does hinder work, but users consent to install adware and, in most cases, can remove it just like any other application. That doesn’t mean it does not endanger users’ systems. On the contrary, it is a real threat. But there is a mediator between adware present on a PC and actual malware harming it – and it is the human user.
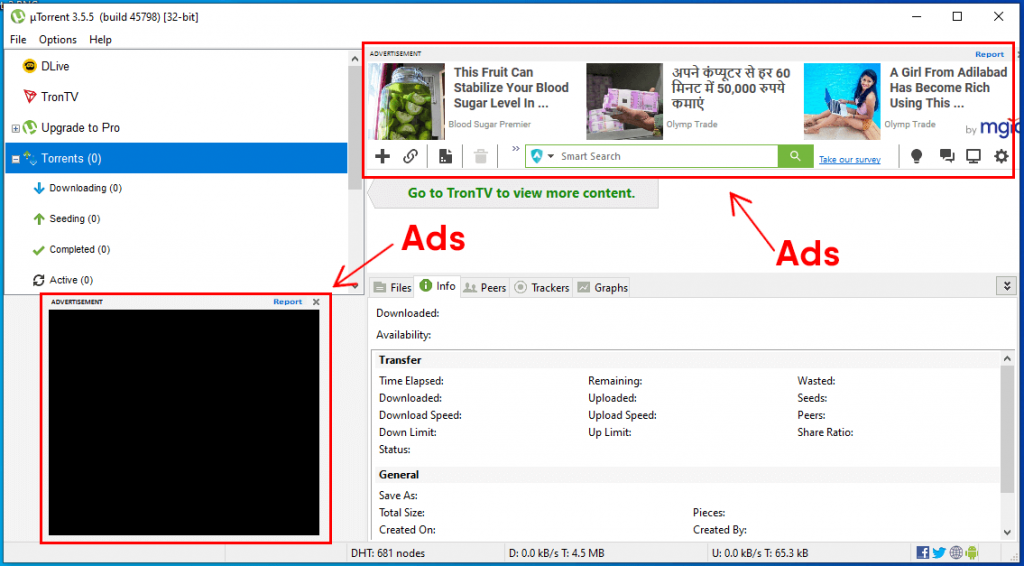
However, many experts put adware alongside malware, since the disputed software obviously brings unwanted experience and blatantly fools users.
Harm and hazard
Adware does harm and poses a threat. Its presence on the PC is self-evident, but it is reckless to underestimate its danger. Such applications are annoying, and they hinder the normal work process. Additional ad panels and popping-up banners reduce the field of view and block the parts of the viewed websites. Some examples of this virus add non-existent text hyperlinks ad hoc to the viewed websites. Adware PUPs consume resources of the system they inhabit, and users experience considerable loss of running speed as they browse the Internet.
The banners and links that malware throws at its victims are unsafe. Adware is a black-market phenomenon, and no law-abiding company would use intrusive advertising to promote its products. Therefore, advertisers who employ these platforms are unscrupulous. Since the victims of such malware are inexperienced at computers and the Internet (otherwise, they would never buy into the malware installation bait,) cybercriminals use adware as a filter. The one who installed it will more likely also click on the malware-related banners.
Unsafe banners can lead to web pages stuffed with malicious scripts or download links that can infect the victim’s PC with Trojan horses carrying harmful payloads. Credulous users can get their systems infected with coin miners, downloaders, key loggers, backdoors, and the nastiest type of malware – ransomware. The spyware threat, already mentioned above, can be constituted by the initial adware app or the downloaded files (a consequence of such vile advertising.).
How does adware find its way to its victims’ computers?
There are two main ways adware takes over normal browsing and Internet-related software. The first option is via false advertising and fraud promises of unseen beneficial features of the advertised programs (browsers, browser add-ons, etc.) The second option for adware is to be installed stealthily, unbeknownst to users, as a well-hidden complement to other software.
Adware examples
How to protect yourself?
- Vigilance and safety rules. Double-check advanced options whenever you install programs. Uncheck all tick-boxes that allow installing unnecessary programs. Don’t click on unknown links and don’t open attachments to unexpected emails.
- Education. Study what is possible and what is impossible in the modern cyber world. Know that modern browsers such as Google Chrome, Mozilla Firefox, Microsoft Edge, and others already possess all the features adware applications usually promise. As for any applications or browser extensions you want to download, always read users’ feedback on them.
- Decent security software. Install an antivirus program – it will make your life much easier. A proper anti-malware warns you about suspicious webpages and blocks access to overtly dangerous ones. On-run protection function will be the pleasant addition which will make your system much more protected. It detects and removes any infectious agent that might end up on your PC. Choose wisely and you will never have various malware on your PC.
- Conscious browsing. Know what you’re up to on the Internet. Don’t allow advertising and clickbait to take over your attention and curiosity. Keep an eye on the latest malware trends – to know where to expect the tricks from cybercriminals.