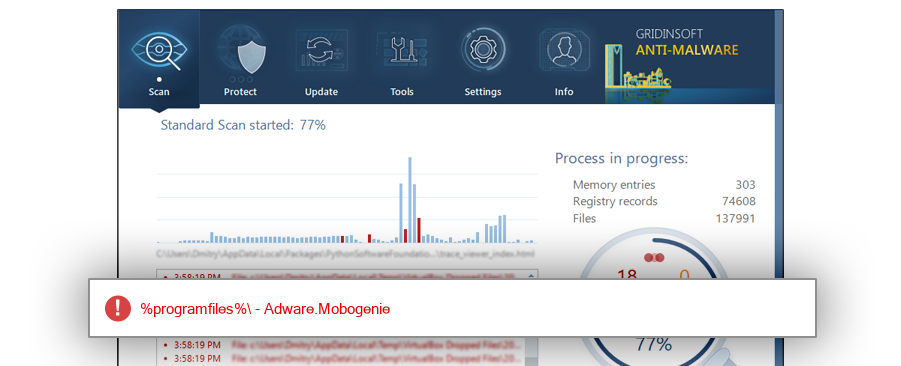
How to remove nsmD971.tmp
- File Details
- Overview
- Analysis
nsmD971.tmp
The module nsmD971.tmp has been detected as Adware.Mobogenie
File Details
| Product Name: |
|
| Company Name: |
|
| MD5: |
f57a690656a8cacfabb78e30d1e71ee1 |
| Size: |
124 KB |
| First Published: |
2017-05-22 10:25:44 (8 years ago) |
| Latest Published: |
2021-12-14 21:49:41 (4 years ago) |
| Status: |
Adware.Mobogenie (on last analysis) |
|
| Analysis Date: |
2021-12-14 21:49:41 (4 years ago) |
Overview
| %programfiles%\mobogenie3 |
| %sysdrive%\windows.old\program files\mobogenie3 |
| %sysdrive%\adwcleaner\quarantine\1xvpfvjcrg |
| %programfiles%\malwareprotectionlive\quarantine |
| %sysdrive%\adwcleaner\quarantine\8yfogkjxrr |
| %programfiles% |
| %sysdrive%\adwcleaner\quarantine |
| %sysdrive%\adwcleaner\quarantine\files |
| %sysdrive%\новая папка |
| %temp%\moboupdate |
| MobogenieService.exe |
| nsmD971.tmp |
| nsg6685.tmp |
| nsd7786.tmp |
| nsq397D.tmp |
| nsp11B4.tmp |
| nsfE037.tmp |
| nsr8492.tmp |
| nse659B.tmp |
| nslF106.tmp |
| nsw95BE.tmp |
| nsrD26E.tmp |
| nslC840.tmp |
| nsqEE5B.tmp |
| nsr1364.tmp |
| nssFB65.tmp |
| nsw9DF.tmp |
| nsuA991.tmp |
| nsu6672.tmp |
| nsg3B09.tmp |
| nsp4176.tmp |
| nsy82AD.tmp |
| nsq77D3.tmp |
| MobogenieService-384ed34a-7776-4569-a692-8985b164e134.exe |
| nsr7B0C.tmp |
| MobogenieService.exe.quarantined |
| nspEE58.tmp |
| nsw5FBF.tmp |
| nsoE052.tmp |
| nsl51AC.tmp |
| nso4871.tmp |
| nss210F.tmp |
| nsgDFF1.tmp |
| nsa27F5.tmp |
| nss800B.tmp |
| nsc5AEF.tmp |
| nsm6375.tmp |
| nsh55A2.tmp |
| nsf3282.tmp |
| nsbECEC.tmp |
| nsi523B.tmp |
| nsw47CD.tmp |
| nsl5C18.tmp |
| nsh7660.tmp |
| nsw2D3B.tmp |
| nso7CA3.tmp |
| nse5297.tmp |
| nsdF20A.tmp |
| nsnF658.tmp |
| nsq5DF5.tmp |
| nsg7081.tmp |
| nsu1F75.tmp |
| nsuE3A1.tmp |
| nsnC925.tmp |
| MobogenieService_IObitDel.exe |
| nseE6E9.tmp |
| nsg245.tmp |
| nsf2CFC.tmp |
| nsaF163.tmp |
| nseF311.tmp |
| nsmB1C5.tmp |
| nsc3FDD.tmp |
| nsbCC38.tmp |
| nswAB81.tmp |
| nsq3959.tmp |
| nsh41CC.tmp |
| nsn1326.tmp |
| nsh7D08.tmp |
| nsj85E6.tmp |
| mobogenieservice.exe |
| nsd6C78.tmp |
| nsdC07A.tmp |
| nsc3553.tmp |
| nsd2A12.tmp |
| nslD1F4.tmp |
| nsp6200.tmp |
| nsvE6E8.tmp |
| nsp13FA.tmp |
| nsvA539.tmp |
| nsjEFDA.tmp |
| nsvD6CC.tmp |
|
9.2% |
|
|
8.9% |
|
|
6.6% |
|
|
6.6% |
|
|
5.5% |
|
|
4.6% |
|
|
3.5% |
|
|
3.2% |
|
|
3.2% |
|
|
3.2% |
|
|
3.2% |
|
|
2.3% |
|
|
2.0% |
|
|
2.0% |
|
|
2.0% |
|
|
1.7% |
|
|
1.7% |
|
|
1.7% |
|
|
1.7% |
|
|
1.4% |
|
|
1.4% |
|
|
1.4% |
|
|
1.4% |
|
|
1.4% |
|
|
1.2% |
|
|
1.2% |
|
|
1.2% |
|
|
1.2% |
|
|
1.2% |
|
|
0.9% |
|
|
0.9% |
|
|
0.9% |
|
|
0.9% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
| Windows 7 |
48.3% |
|
| Windows 10 |
32.0% |
|
| Windows 8.1 |
9.1% |
|
| Windows XP |
4.6% |
|
| Windows 8 |
4.0% |
|
| Windows Vista |
1.4% |
|
| Windows Embedded Standard |
0.6% |
|
Analysis
| Subsystem: |
Windows GUI |
| PE Type: |
pe |
| OS Bitness: |
32 |
| Image Base: |
0x00400000 |
| Entry Address: |
0x00014baa |
| Name |
Size of data |
MD5 |
| .text |
87552 |
6eda92e8652b0da66c338355b09f04b7 |
| .rdata |
26112 |
65babb4665b391d4486aa40b7f93608e |
| .data |
2048 |
f9a2832e906f2a348e49a3f757729fd1 |
| .rsrc |
1536 |
708d02327b3af6147c4f4854c21f2be3 |
| .reloc |
5632 |
f3000326b33263114935bdb5f04967a6 |