How to remove dwhb7dd.exe
- File Details
- Overview
- Analysis
dwhb7dd.exe
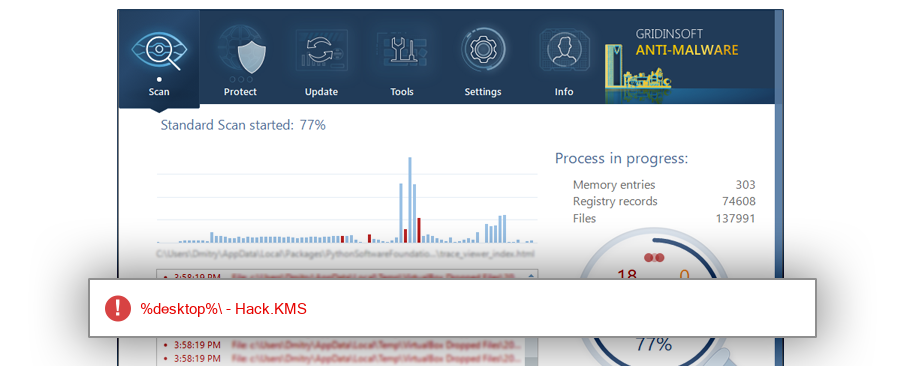
The module dwhb7dd.exe has been detected as Possible Threat
File Details
| Product Name: |
|
| Company Name: |
|
| MD5: |
311f3baa9bfa5b2364fea8b254d15eb9 |
| Size: |
8 MB |
| First Published: |
2017-05-21 05:04:48 (8 years ago) |
| Latest Published: |
2025-11-13 23:01:14 (3 months ago) |
| Status: |
Possible Threat (on last analysis) |
|
| Analysis Date: |
2025-11-13 23:01:14 (3 months ago) |
Overview
| Signed By: |
WZT |
| Status: |
Invalid (digital signature could be stolen or file could be patched) |
| %profile%\downloads\kmsa.rar |
| %profile%\downloads |
| %commonappdata%\kmsautos |
| %sysdrive%\activators\kmsauto net 2015 v1.4.2 portable |
| %desktop%\win 10 |
| %commonappdata%\kmsauto |
| %profile%\downloads\[always2mile]kmsan (1) |
| %profile%\downloads\[always2mile]kmsan |
| %profile%\downloads\activador de windows 10-marlon tutos\activador de windows 10-marlon tutos\activador de windows 10 |
| %sysdrive%\$recycle.bin\s-1-5-21-4050879837-1267410179-457611355-1000\$rbaf9na\activador de windows 10-marlon tutos\activador de windows 10 |
| KMSAuto Net.exe |
| dwhb7dd.exe |
| Windows @amp; Office activator.exe |
| $RTWLVEN.exe |
| KMSAuto.exe |
| KMSAuto Net_SoftGozar.com.exe |
| gKMSAuto Net.exe |
| KMSAuto Net (2017_07_10 18_21_05 UTC).exe |
| LocaldZQbotQCnA.exe |
| KMSAuto Net.exe.quarantine |
| KMSAuto Net - Copy.exe |
| KMSAuto Net.exe.quarantined |
| kmsautonet.exe |
| kmsauto net.exe |
| $R8S2BGF.exe |
| $R4HKXJM.exe |
| KMSAuto Net 2015 1.4.2.exe |
| dwh7ef8.exe |
| $RFMNRJM.exe |
| $R3TUBB2.exe |
| KMSAuto Net (1).exe |
| A0005654.exe |
| A0020185.exe |
| $RQVH32N.exe |
|
15.6% |
|
|
14.1% |
|
|
9.4% |
|
|
5.5% |
|
|
4.3% |
|
|
3.7% |
|
|
3.3% |
|
|
3.2% |
|
|
3.1% |
|
|
2.6% |
|
|
2.5% |
|
|
1.8% |
|
|
1.8% |
|
|
1.8% |
|
|
1.7% |
|
|
1.6% |
|
|
1.3% |
|
|
1.1% |
|
|
1.1% |
|
|
1.0% |
|
|
0.9% |
|
|
0.9% |
|
|
0.8% |
|
|
0.8% |
|
|
0.7% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
| Windows 10 |
66.9% |
|
| Windows 7 |
23.8% |
|
| Windows 8.1 |
7.1% |
|
| Windows 8 |
1.0% |
|
| Windows XP |
0.4% |
|
| Windows Server 2012 R2 |
0.2% |
|
| Windows Vista |
0.1% |
|
| Windows Embedded 8.1 |
0.1% |
|
| Windows Server 2012 |
0.1% |
|
| Windows Server 2008 R2 |
0.1% |
|
Analysis
| Subsystem: |
Windows GUI |
| PE Type: |
pe |
| OS Bitness: |
32 |
| Image Base: |
0x00400000 |
| Entry Address: |
0x0088f916 |
| MVID: |
7892deb7-dada-421c-bc20-7e74a06b300b |
| Typelib ID: |
fcaa9736-cfc3-43fa-33da-378396c3a336 |
| Name |
Size of data |
MD5 |
| .text |
8968704 |
49da5bb8359193aac3b6d3a5c9fb5475 |
| .rsrc |
48640 |
11537e94aaa0da3f1cb72153f3a9eded |
| .reloc |
512 |
ab79c241760153c3b32b904b4258762b |