How to remove autopico.exe
- File Details
- Overview
- Analysis
autopico.exe
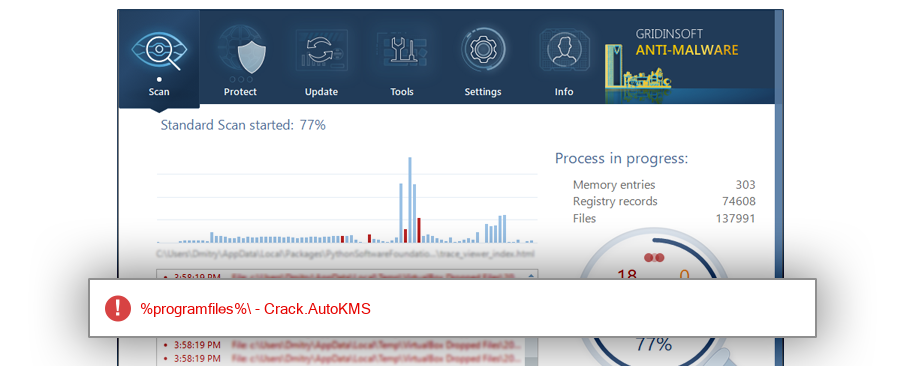
The module autopico.exe has been detected as Crack.AutoKMS
File Details
| Product Name: |
|
| Company Name: |
|
| MD5: |
e457a67454f64ea98474452b8a6df20f |
| Size: |
720 KB |
| First Published: |
2017-05-21 12:05:37 (8 years ago) |
| Latest Published: |
2025-06-20 23:10:41 (9 months ago) |
| Status: |
Crack.AutoKMS (on last analysis) |
|
| Analysis Date: |
2025-06-20 23:10:41 (9 months ago) |
Overview
| %programfiles%\kmspico |
| %programfiles%\microsoft office\root\crack\kmspico |
| %desktop%\新增資料夾 |
| %desktop%\programmi 2016\attivatori\kmspico 10.1.6 final + portable (office and windows 10 activator)\kms1016f_p.rar\kmspico 10.1.6 final + portable (office and windows 10 activator)\kmspico portable |
| %programfiles%\microsoft office 15\kmspico portable |
| %programfiles%\microsoft office\kmspico portable |
| %profile%\downloads\compressed\kmspico portable active windows 7,8,10 - thuthuattienich.com\kmspico portable active windows 10 - thuthuattienich.com |
| %profile%\downloads\katilimsiz aio mart 2017\katilimsiz aio mart 2017\programlar\ks1016.sane\kmspico portable |
| %sysdrive%\$recycle.bin\s-1-5-21-977091263-3761003994-473994326-1000\$rz9q57b.rar\kmspico_v10.1.6\kmspico_v10.1.6\kmspico portable |
| %sysdrive%\$recycle.bin\s-1-5-21-977091263-3761003994-473994326-1000\$ryu7e79.6\kmspico_v10.1.6\kmspico portable |
| AutoPico.exe |
| autopico.exe |
| trzEB25.tmp |
| trz14BB.tmp |
| AutoPico(53204).exe |
| gAutoPico.exe |
| $RS4HUY9.exe |
|
22.5% |
|
|
10.5% |
|
|
6.2% |
|
|
5.0% |
|
|
5.0% |
|
|
3.4% |
|
|
3.3% |
|
|
3.1% |
|
|
2.5% |
|
|
2.2% |
|
|
2.2% |
|
|
2.1% |
|
|
1.7% |
|
|
1.6% |
|
|
1.6% |
|
|
1.6% |
|
|
1.3% |
|
|
1.2% |
|
|
1.2% |
|
|
1.2% |
|
|
1.1% |
|
|
1.1% |
|
|
1.1% |
|
|
1.1% |
|
|
1.0% |
|
|
0.8% |
|
|
0.6% |
|
|
0.6% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
| Windows 10 |
64.3% |
|
| Windows 7 |
26.2% |
|
| Windows 8.1 |
7.5% |
|
| Windows 8 |
0.7% |
|
| Windows Server 2012 R2 |
0.7% |
|
| Windows XP |
0.3% |
|
| Windows Vista |
0.1% |
|
Analysis
| Subsystem: |
Windows GUI |
| PE Type: |
pe |
| OS Bitness: |
32 |
| Image Base: |
0x00400000 |
| Entry Address: |
0x000b3d8e |
| MVID: |
d69b3be7-e19c-4c6c-9d56-55e220b36784 |
| Name |
Size of data |
MD5 |
| .text |
728576 |
bb9de00ee32879e2e1a9046f294135a6 |
| .rsrc |
4096 |
ee1ad21a56f9c001f36d2f5c9d892fb8 |
| .reloc |
512 |
fac434cb7192fdf33e9181f77fd6e090 |