How to remove MaxxAudioRender64.dll
- File Details
- Overview
- Analysis
MaxxAudioRender64.dll
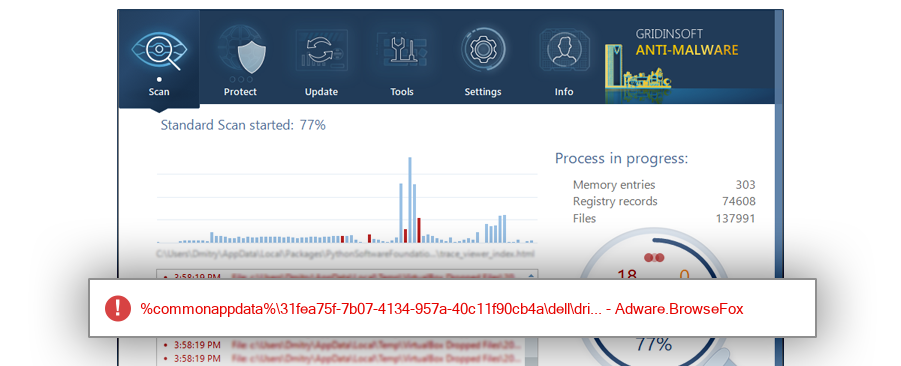
The module MaxxAudioRender64.dll has been detected as Adware.BrowseFox
File Details
| Product Name: |
|
| Company Name: |
|
| MD5: |
cd28e004433544e51b8a56c577848c9b |
| Size: |
22 MB |
| First Published: |
2017-05-21 16:04:42 (7 years ago) |
| Latest Published: |
2019-03-26 00:19:33 (6 years ago) |
| Status: |
Adware.BrowseFox (on last analysis) |
|
| Analysis Date: |
2019-03-26 00:19:33 (6 years ago) |
| %commonappdata%\40e4509d-93ba-4fdd-82c6-1f8445099ea3\dell\drivers\audio_driver_7877m_wn32_6.0.1.7989_a04\realtekhdaudio\win64 |
| %commonappdata%\55d1c1d8-68b7-4f45-a1d4-2e298f0fb658\dell\drivers\audio_driver_7877m_wn32_6.0.1.7989_a04\realtekhdaudio\win64 |
| %commonappdata%\5c845706-ff23-4f99-b621-f9f45295de0d\dell\drivers\audio_driver_7877m_wn32_6.0.1.7989_a04 (1)\realtekhdaudio\win64 |
| %commonappdata%\a1975901-9fd6-4919-a258-61affebce12f\dell\drivers\audio_driver_7877m_wn32_6.0.1.7989_a04\realtekhdaudio\win64 |
| %commonappdata%\1d3c3e3d-cbc6-41ba-a870-d492a63261ef\dell\drivers\audio_driver_7877m_wn32_6.0.1.7989_a04\realtekhdaudio\win64 |
| %commonappdata%\386c81bc-09d4-4e8b-9032-f9765d160846\dell\drivers\audio_driver_7877m_wn32_6.0.1.7989_a04\realtekhdaudio\win64 |
| %commonappdata%\abe72e54-ee2f-427f-a0de-87efc4d403ba\dell\drivers\audio_driver_7877m_wn32_6.0.1.7989_a04\realtekhdaudio\win64 |
| %commonappdata%\92447115-c4ab-4d93-9732-459b4e170201\dell\drivers\audio_driver_7877m_wn32_6.0.1.7989_a04\realtekhdaudio\win64 |
| %commonappdata%\042d7438-f636-4cce-8e25-2fabf87b491a\dell\drivers\audio_driver_177vg_wn32_6.0.1.7989_a03\realtekhdaudio\win64 |
| %commonappdata%\fea332a2-55bd-4aa8-9042-1caecb9a6344\dell\drivers\audio_driver_7877m_wn32_6.0.1.7989_a04\realtekhdaudio\win64 |
|
50.0% |
|
|
22.7% |
|
|
9.1% |
|
|
4.5% |
|
|
4.5% |
|
|
4.5% |
|
|
4.5% |
|
Analysis
| Subsystem: |
Windows GUI |
| PE Type: |
pe |
| OS Bitness: |
64 |
| Image Base: |
0x0000000180000000 |
| Entry Address: |
0x0125aab4 |
| Name |
Size of data |
MD5 |
| RT_CODE |
939008 |
df2023f54219bd58f9777d0e16fe4efd |
| .text |
18425856 |
7df44dc78f103c19b2cedaf38389050a |
| IPPCODE |
538624 |
ce11867218b09ba794d96422bd2e784f |
| .rdata |
2635776 |
b06ef8083e6db7e4aad395186bdecf0f |
| .data |
133632 |
1ce54b300cc8f7b24f3f47ab6826bca8 |
| .pdata |
267776 |
93103e8857975cde523d938bbe6e3348 |
| RT_CONST |
2048 |
397d8ec1855945760dab24b20dd4999c |
| .data1 |
71168 |
142baefb169140f9f3c7e0acb1757578 |
| RT_DATA |
16384 |
e0e23775e54b3202f02c619b04cc09e0 |
| .debug_o |
106496 |
b13cdac5f553c82846782e173f7d260e |
| .gfids |
512 |
e77f966bea35e96a43b7d43972e8f93c |
| IPPDATA |
1536 |
cbae23c9ad53f22c54a02422da5368e5 |
| .tls |
512 |
bf619eac0cdf3f68d496ea9344137e8b |
| .trace |
31744 |
73642b03568ce5adb778ee749a84a3a2 |
| _RDATA |
4608 |
1a7e99672797886858bd7bf848b03f20 |
| .rsrc |
17408 |
30b3b90bcba8bff59ac5e7647420aa48 |
| .reloc |
30208 |
e7e61d32fa2d24a0bad521861d082243 |