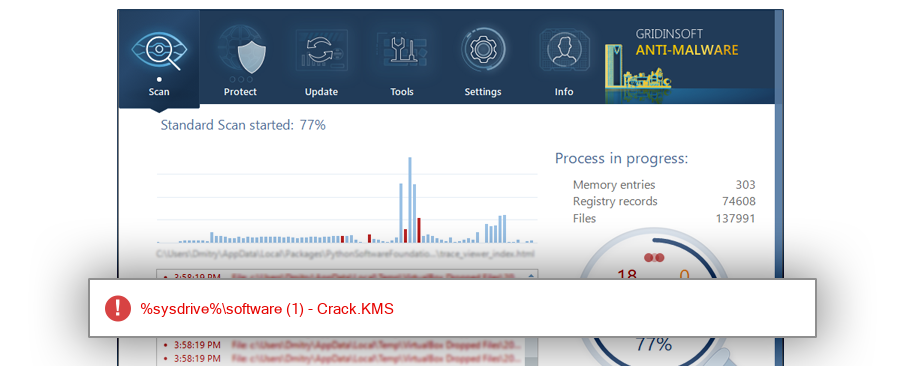
How to remove KMSAuto Net.exe
- File Details
- Overview
- Analysis
KMSAuto Net.exe
The module KMSAuto Net.exe has been detected as Crack.KMS
File Details
| Product Name: |
|
| Company Name: |
|
| MD5: |
2fb86be791b4bb4389e55df0fec04eb7 |
| Size: |
8 MB |
| First Published: |
2017-05-22 07:06:14 (8 years ago) |
| Latest Published: |
2026-01-28 23:01:26 (3 weeks ago) |
| Status: |
Crack.KMS (on last analysis) |
|
| Analysis Date: |
2026-01-28 23:01:26 (3 weeks ago) |
Overview
| Signed By: |
WZTeam |
| Status: |
Valid |
| %profile%\downloads\microsoft office 2016 pro plus.may.2017.32-64x\microsoft office 2016 pro plus.may.2017.64x |
| %commonappdata%\kmsauto |
| %sysdrive%\programdata |
| %commonappdata%\kmsautos |
| %profile%\downloads\compressed\kms.anet.p.2016.1.4.9.indo-cybershare\kmsauto.net.2016.1.4.9.portable |
| %profile%\desktop |
| %mydoc%\[bao](9864)andreikarenin-roaldekbergpt.1,2-816p\kmsauto-net-1.4.9 |
| %profile%\downloads\microsoft office professional plus 2016 april 2017 [cracksnow]\x64\setup + activator |
| %profile%\downloads\microsoft office professional plus 2016 april 2017 [cracksnow]\x32\setup + activator |
| %desktop%\nouveau dossier (2)\kmsauto net 2016 v1.4.9 portable |
| Activator.exe |
| KMSAuto Net.exe |
| KMSAuto Net (@WdsX7@).exe |
| KMSAuto Net (@WdsX7@) (1).exe |
| $R8YXO8L.exe |
| KMSAuto_Net.exe |
| KMSAuto |
| $RB7794L.exe |
| KMSAuto Net 2015 v1.4.9 Final.exe |
| KMSAutoNetPatcher.exe |
| Aktywator.exe |
| dwh491a.exe |
| KMSAuto.Net.2016_1.4.9_YasDL.com.exe |
| patch.exe |
| DTAW.exe |
| $RWOWDJ3.exe |
| Activator (2017_04_03 18_30_13 UTC).exe |
| Activator (2017_05_14 04_17_08 UTC).exe |
| Activator (2017_04_19 00_46_31 UTC).exe |
| Activador Windows 10 - Fix Up Pc.exe |
| $RF1RT56.exe |
| $R3YXC88.exe |
| $RVORJYX.exe |
| $RHEPESL.exe |
| $ROH8PUU.exe |
| $RZSW9JM.exe |
| $R8Y9NW2.exe |
| $R0E3WDA.exe |
| kmsauto net.exe |
| KMSAuto Net_IObitDel.exe |
| KMSAutoNet.exe |
| $RVY5G6Z.exe |
| KMSAUTO NET.EXE |
| KMSAuto_Net_Downloadly.ir.exe |
|
15.6% |
|
|
8.8% |
|
|
4.8% |
|
|
4.2% |
|
|
3.9% |
|
|
3.4% |
|
|
2.9% |
|
|
2.7% |
|
|
2.4% |
|
|
2.4% |
|
|
2.1% |
|
|
1.8% |
|
|
1.8% |
|
|
1.7% |
|
|
1.7% |
|
|
1.6% |
|
|
1.6% |
|
|
1.6% |
|
|
1.5% |
|
|
1.5% |
|
|
1.5% |
|
|
1.4% |
|
|
1.4% |
|
|
1.2% |
|
|
1.1% |
|
|
1.0% |
|
|
1.0% |
|
|
0.9% |
|
|
0.8% |
|
|
0.8% |
|
|
0.7% |
|
|
0.7% |
|
|
0.7% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
| Windows 10 |
69.7% |
|
| Windows 7 |
20.8% |
|
| Windows 8.1 |
7.5% |
|
| Windows 8 |
0.5% |
|
| Windows Server 2012 R2 |
0.5% |
|
| Windows Server 2008 R2 |
0.3% |
|
| Windows XP |
0.2% |
|
| Windows Embedded 8.1 |
0.1% |
|
| Windows Server 2016 |
0.1% |
|
| Windows Server 2012 |
0.1% |
|
| Windows Vista |
0.1% |
|
Analysis
| Subsystem: |
Windows GUI |
| PE Type: |
pe |
| OS Bitness: |
32 |
| Image Base: |
0x00400000 |
| Entry Address: |
0x00851422 |
| MVID: |
c5567ba3-c7d7-41cb-8f43-c2cdbd67e27a |
| Typelib ID: |
fcaa9736-cfc3-43fa-33da-378396c3a336 |
| Name |
Size of data |
MD5 |
| .text |
8713728 |
05c42fbc0ada2d3e3b761a0df990816f |
| .rsrc |
48640 |
aba2552fc80221395b87b453e62cea49 |
| .reloc |
512 |
40538ff226cbeeb2a3b88fe2d27b5fc9 |