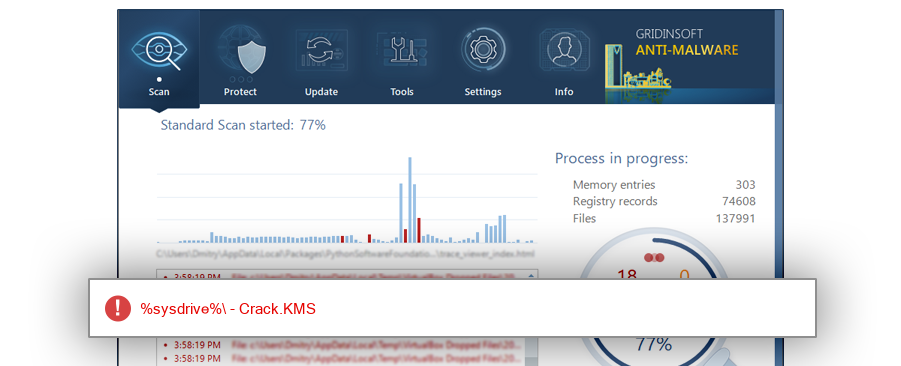
How to remove Activator.exe
- File Details
- Overview
- Analysis
Activator.exe
The module Activator.exe has been detected as Crack.KMS
File Details
| Product Name: |
|
| Company Name: |
|
| MD5: |
d02b35945c18e89dc3bb43bc7f6153be |
| Size: |
8 MB |
| First Published: |
2017-05-21 09:01:36 (8 years ago) |
| Latest Published: |
2024-07-08 23:02:09 (2 years ago) |
| Status: |
Crack.KMS (on last analysis) |
|
| Analysis Date: |
2024-07-08 23:02:09 (2 years ago) |
Overview
| Signed By: |
WZTeam |
| Status: |
Invalid (digital signature could be stolen or file could be patched) |
| %commonappdata%\kmsautos |
| %profile%\downloads\kmsauto net 2016 v1.5.0 multilingual portable\kmsauto net 2016 v1.5.0 portable |
| %temp%\rar$exa0.163\kmsauto net 2016 v1.5.0.kuyhaa |
| %profile%\downloads\kmsauto net 2016 v1.5.0.kuyhaa |
| %desktop%\indirilenler\programs\kmsauto_net_2016_v1.5.0_portable.rar |
| %commonappdata%\kmsauto |
| %profile%\downloads |
| %profile%\downloads\kmsauto net 2016 v1.5.0.rar\kmsauto net 2016 v1.5.0 |
| %profile%\downloads\kmsauto net |
| %profile%\downloads\kmsauto net 2016 v1.5.0 |
| KMSAuto Net.exe |
| Activator.exe |
| kmsautonet.exe |
| HpupbKVF.exe |
| KMSAuto_Net.exe |
| KMSAuto Net_origin.exe |
| Attivatore_Nuovo.exe |
| KMSAuto Net (2017_09_08 22_28_09 UTC).exe |
| kmsauto net.exe |
| A0369121.exe |
| KMSAuto Net 2016 v1.5.0.exe |
| $RUUWMT4.exe |
| KMSAuto Net 2016 1.5.0.exe |
| KMSAUTO NET.EXE |
| $R5LI1RS.exe |
| KMSAuto myegy.exe |
| Setup.exe |
| $RA8A6CY.exe |
| dwh11e6.exe |
| dwh3154.exe |
| KMSAuto Net 2016_1.5.exe |
| $RP6KB4C.exe |
| A0020845.exe |
|
15.0% |
|
|
14.1% |
|
|
13.6% |
|
|
9.8% |
|
|
3.9% |
|
|
3.8% |
|
|
3.2% |
|
|
2.8% |
|
|
2.2% |
|
|
2.2% |
|
|
1.9% |
|
|
1.7% |
|
|
1.7% |
|
|
1.7% |
|
|
1.3% |
|
|
1.3% |
|
|
1.2% |
|
|
1.1% |
|
|
1.0% |
|
|
1.0% |
|
|
0.7% |
|
|
0.7% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.4% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
| Windows 10 |
69.1% |
|
| Windows 7 |
20.1% |
|
| Windows 8.1 |
7.4% |
|
| Windows 8 |
1.1% |
|
| Windows Server 2012 R2 |
1.0% |
|
| Windows XP |
0.6% |
|
| Windows Server 2008 R2 |
0.5% |
|
| Windows Embedded 8.1 |
0.1% |
|
Analysis
| Subsystem: |
Windows GUI |
| PE Type: |
pe |
| OS Bitness: |
32 |
| Image Base: |
0x00400000 |
| Entry Address: |
0x00883dc2 |
| MVID: |
bbda16cd-a2f2-4e32-9d95-d67d1bc12b14 |
| Typelib ID: |
fcaa9736-cfc3-43fa-33da-378396c3a336 |
| Name |
Size of data |
MD5 |
| .text |
8920576 |
44e37a3fc7a2048df8e06ee5ddc872f2 |
| .rsrc |
48640 |
dbb1c7fe817ea7488fd717547d7792c1 |
| .reloc |
512 |
9af220b927123ad1a5da0fde53cb18ec |