How to remove ActOffice.exe
- File Details
- Overview
- Analysis
ActOffice.exe
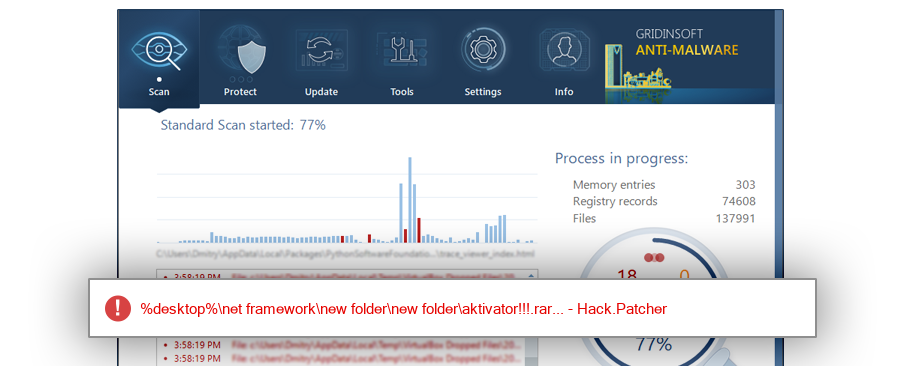
The module ActOffice.exe has been detected as Hack.Patcher
File Details
| Product Name: |
|
| MD5: |
292ff22aec228b1ac75730c25080cead |
| Size: |
1 MB |
| First Published: |
2017-05-22 03:00:36 (8 years ago) |
| Latest Published: |
2025-12-15 23:00:47 (a month ago) |
| Status: |
Hack.Patcher (on last analysis) |
|
| Analysis Date: |
2025-12-15 23:00:47 (a month ago) |
| %profile%\downloads\ativadores windows 7.rar\ativadores windows 7\re-loader activator 1.6 final |
| %sysdrive%\activators\re-loader activator 1.6 final |
| %desktop%\aktivator!!! |
| %programfiles%\microsoft office\act |
| %profile%\downloads\microsoft office professional plus 2016 v16.0.4405.1000 july 2016 incl activator-=team os=-\re-loaderbyr@1n.rar |
| %profile%\downloads\compressed\ฟอนต์\717a1f7b7a371658a84e0202d64fab9c.rar |
| %sysdrive%\soft + driver + tool activate\activate windows + office |
| %sysdrive%\$recycle.bin\s-1-5-21-2035648585-4018777253-4007630945-1001\$rgycolq.6final |
| %sysdrive%\$recycle.bin\s-1-5-21-2035648585-4018777253-4007630945-1001\$r7vbk62.zip |
| %desktop%\==bonus==\re-loader activator 1.6 final |
| Re-LoaderByR@1n.exe |
| ActOffice.exe |
| iBDA3GATE.COM_Re-LoaderByR@1n.exe |
| Re-Loader Activator 1.6.3 Final.exe |
| windows10-loader.exe |
| Re-Loader.exe |
| Patch.exe |
| Re.exe |
| start_here.exe |
| $RBPA8EO.exe |
| actoffice.exe |
| 123.exe |
| $RLNXENQ.exe |
| 888.exe |
| Re-Loader - mhktricks.net.exe |
| Re-Loader.EXE |
| gRe-LoaderByR@1n.exe |
| Activator.exe |
| vActOffice.exe |
| Re-Loader win 10,Office 13,16.exe |
| Re-Loader 1.6.exe |
|
26.1% |
|
|
7.4% |
|
|
5.1% |
|
|
5.0% |
|
|
4.7% |
|
|
4.6% |
|
|
4.0% |
|
|
3.5% |
|
|
3.4% |
|
|
2.5% |
|
|
2.5% |
|
|
2.0% |
|
|
2.0% |
|
|
1.9% |
|
|
1.8% |
|
|
1.5% |
|
|
1.4% |
|
|
1.3% |
|
|
1.1% |
|
|
0.9% |
|
|
0.9% |
|
|
0.9% |
|
|
0.9% |
|
|
0.9% |
|
|
0.9% |
|
|
0.8% |
|
|
0.7% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.5% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
| Windows 10 |
66.0% |
|
| Windows 7 |
29.8% |
|
| Windows 8.1 |
3.0% |
|
| Windows Embedded 8.1 |
0.4% |
|
| Windows Server 2012 R2 |
0.4% |
|
| Windows XP |
0.2% |
|
| Windows 8 |
0.1% |
|
| Windows Server 2008 R2 |
0.1% |
|
Analysis
| Subsystem: |
Windows GUI |
| PE Type: |
pe |
| OS Bitness: |
32 |
| Image Base: |
0x00400000 |
| Entry Address: |
0x00002e5e |
| Name |
Size of data |
MD5 |
| .text |
4096 |
4f3963036a62a34c1b58def87fdc568d |
| .rsrc |
36864 |
19365e2563c069c2e2a80e14a9462e4d |
| .reloc |
512 |
d2eb843144bc74a04f2897f18f705068 |