How to remove $RQN60U6.exe
- File Details
- Overview
- Analysis
$RQN60U6.exe
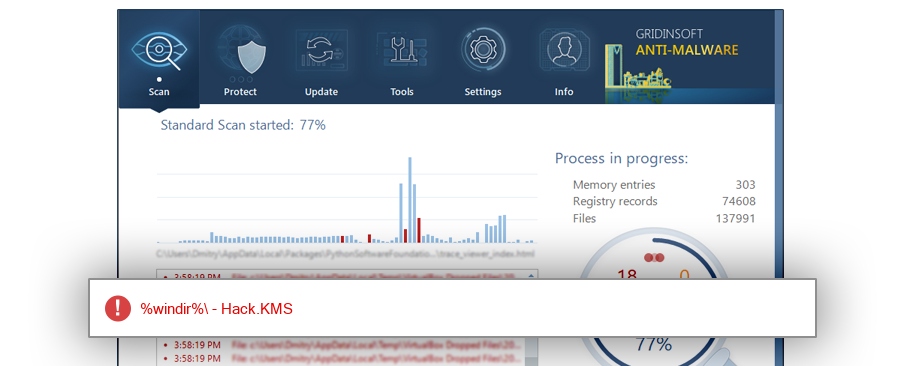
The module $RQN60U6.exe has been detected as Hack.KMS
File Details
| MD5: |
0f9fd9565e6eb157fa9be11ed9c1dc9f |
| Size: |
25 KB |
| First Published: |
2017-05-21 03:01:57 (8 years ago) |
| Latest Published: |
2025-12-23 23:01:30 (a month ago) |
| Status: |
Hack.KMS (on last analysis) |
|
| Analysis Date: |
2025-12-23 23:01:30 (a month ago) |
| %sysdrive%\windows |
| %appdata%\zhp\quarantine |
| %sysdrive%\windows.old\windows |
| %sysdrive%\system recovery\repair\backup |
| %sysdrive%\system volume information\systemrestore\frstaging\windows |
| %commonappdata%\emco\network malware cleaner 6\storage\quarantined threats\suspicious threats\chiara-pc\suspicious threat 4450\rootkit\file\windir |
| %commonappdata%\emco\network malware cleaner 6\storage\quarantined threats\suspicious threats\luana-pc\suspicious threat 412\rootkit\file\windir |
| %commonappdata%\emco\network malware cleaner 6\storage\quarantined threats\suspicious threats\luana-pc\suspicious threat 3898\rootkit\file\windir |
| %sysdrive%\$recycle.bin\s-1-5-21-3903732087-1911127918-809877525-1001 |
| %sysdrive%\$recycle.bin\s-1-5-21-3377759190-1378281995-3082478433-1001 |
| KMS-R@1n.exe |
| kms-r@1n.exe |
| FB205252C895DBBDDE04B0429941C651D51C8F12.exe |
| KMS-R@1n(91).exe |
| KMS-R@1n_bk.exe |
| KMS-R@1n.exe.quarantined |
| $RB9A64O.exe |
| $RZOYGWV.exe |
| KMS-R@1n(1433).exe |
| $RIUWHK7.exe |
| $R2YVJV1.exe |
| $RT5Y1J4.exe |
| $ROGW01D.exe |
| KMS-R@1N.del |
| $RVSR9QQ.exe |
| $RI3BMU7.exe |
| $R7MIRB8.exe |
| $RQWB3DT.exe |
| 11111....exe |
| KMS-R@1n.exe.q_Quarantine_2CF6600_q |
| KMS-R@1n(3).exe |
| $R0WJBSK.exe |
| {3BF16B0E-62E3-4487-8476-30BAF61CFB19} |
| $R50G15Y.exe |
| 2495E5BCD4E6121B.vir |
| 6417BEB774F051E0.vir |
| $R1HXAQ5.exe |
| $RZA3XBP.exe |
| KMS-R@1n.VIR |
| $RQN60U6.exe |
|
17.6% |
|
|
9.1% |
|
|
8.5% |
|
|
7.0% |
|
|
7.0% |
|
|
6.1% |
|
|
5.4% |
|
|
2.5% |
|
|
2.5% |
|
|
2.1% |
|
|
1.8% |
|
|
1.8% |
|
|
1.4% |
|
|
1.3% |
|
|
1.2% |
|
|
1.2% |
|
|
1.1% |
|
|
1.0% |
|
|
0.9% |
|
|
0.9% |
|
|
0.7% |
|
|
0.7% |
|
|
0.7% |
|
|
0.7% |
|
|
0.7% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
| Windows 10 |
79.6% |
|
| Windows 7 |
14.2% |
|
| Windows 8.1 |
5.1% |
|
| Windows 8 |
0.6% |
|
| Windows Server 2012 R2 |
0.2% |
|
| Windows Server 2016 |
0.2% |
|
| Windows Vista |
0.1% |
|
| Windows Embedded 8.1 |
0.1% |
|
Analysis
| Subsystem: |
Windows CUI |
| PE Type: |
pe |
| OS Bitness: |
64 |
| Image Base: |
0x0000000140000000 |
| Entry Address: |
0x000030e4 |
| Name |
Size of data |
MD5 |
| .text |
8704 |
010b3216a1b2d2bbfc534ae515ab26a6 |
| .rdata |
10752 |
fdeaef32ab18e3ca3fb52e395afd68d7 |
| .data |
3072 |
27861e636a3d4cce16d909ec08b2f43b |
| .pdata |
512 |
4fe33dd7d5ee4c11c4b6715e0a589498 |
| .rsrc |
1536 |
1a4372f1b43f082c357b9ee44dd5dc4f |
| .reloc |
512 |
43434ed5dc93aa6c5aa41a6c1bc03a8a |