How to remove $RKWOYIY.sys
- File Details
- Overview
- Analysis
$RKWOYIY.sys
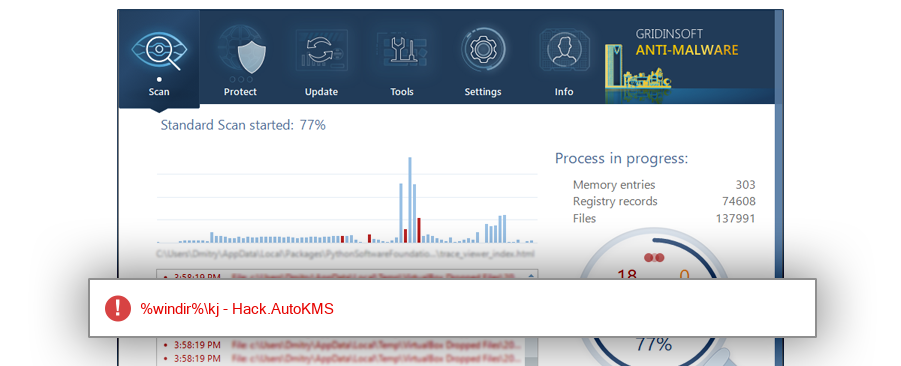
The module $RKWOYIY.sys has been detected as Hack.AutoKMS
File Details
| Product Name: |
|
| Company Name: |
|
| MD5: |
fb1c2fd15bf77e0e08eb5b71e179de80 |
| Size: |
8 KB |
| First Published: |
2017-05-25 09:03:48 (8 years ago) |
| Latest Published: |
2025-02-22 23:01:35 (a year ago) |
| Status: |
Hack.AutoKMS (on last analysis) |
|
| Analysis Date: |
2025-02-22 23:01:35 (a year ago) |
| %temp%\7zipsfx.001\bios_emulator |
| %windir%\kj\bios_emulator |
| %system%\drivers |
| %temp%\7zipsfx.000\bios_emulator |
| %sysdrive%\temp\7zipsfx.000\bios_emulator |
| %sysdrive%\windows.old\windows\kj\bios_emulator |
| %temp%\7zipsfx.002\bios_emulator |
| %temp%\7zipsfx.003\bios_emulator |
| %windir%\kj |
| %sysdrive%\0backup\program\k.j_130319\k.j_130319.exe |
| royal32.sys |
| $RKWOYIY.sys |
| oem-drv86.sys |
|
20.2% |
|
|
9.9% |
|
|
9.4% |
|
|
9.4% |
|
|
6.9% |
|
|
4.9% |
|
|
3.4% |
|
|
3.4% |
|
|
2.5% |
|
|
2.0% |
|
|
2.0% |
|
|
2.0% |
|
|
1.5% |
|
|
1.5% |
|
|
1.0% |
|
|
1.0% |
|
|
1.0% |
|
|
1.0% |
|
|
1.0% |
|
|
1.0% |
|
|
1.0% |
|
|
1.0% |
|
|
1.0% |
|
|
1.0% |
|
|
1.0% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
| Windows 7 |
58.7% |
|
| Windows 10 |
17.0% |
|
| Windows 8 |
15.0% |
|
| Windows 8.1 |
7.8% |
|
| Windows Server 2003 |
0.5% |
|
| Windows XP |
0.5% |
|
| Windows Server 2008 R2 |
0.5% |
|
Analysis
| Subsystem: |
Native |
| PE Type: |
pe |
| OS Bitness: |
32 |
| Image Base: |
0x00010000 |
| Entry Address: |
0x000041d6 |
| Name |
Size of data |
MD5 |
| .text |
3072 |
0bc0cda3383877fa4de55b6be92f211d |
| .rdata |
1024 |
2dcd12102946023c50643d31aea50ffd |
| .data |
512 |
83aaef3a426d8c7233ab63583d1fa00a |
| INIT |
1024 |
a1d151d8a801fa95e405c27c82ccb20f |
| .rsrc |
1536 |
80bb1429515120be3f282f4300bb9987 |
| .reloc |
512 |
1d1a543c87f779d88eda45d8a989c8ed |