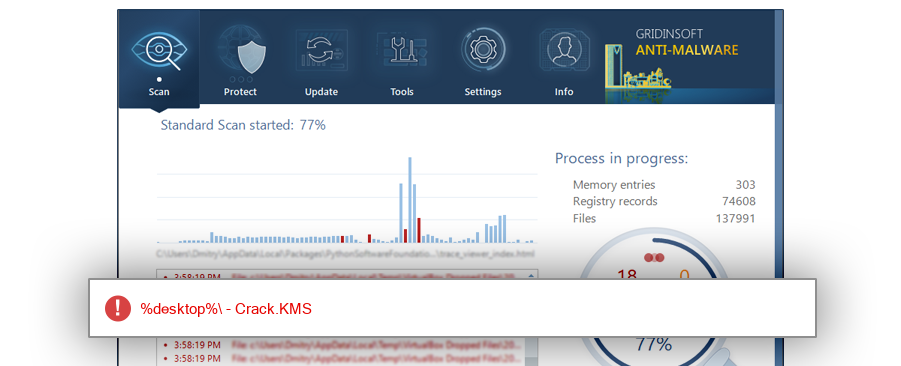
How to remove $RDJ41CE.exe
- File Details
- Overview
- Analysis
$RDJ41CE.exe
The module $RDJ41CE.exe has been detected as Crack.KMS
File Details
| Product Name: |
|
| Company Name: |
|
| MD5: |
fd743b55d530e0468805de0e83758fe9 |
| Size: |
8 MB |
| First Published: |
2017-11-03 23:05:12 (8 years ago) |
| Latest Published: |
2026-02-06 23:01:43 (2 weeks ago) |
| Status: |
Crack.KMS (on last analysis) |
|
| Analysis Date: |
2026-02-06 23:01:43 (2 weeks ago) |
Overview
| Signed By: |
WZTeam |
| Status: |
Valid |
| %commonappdata%\kmsautos |
| %temp%\bnz.59fd62511d23337b |
| %commonappdata%\kmsauto |
| %desktop%\downloads\ratiborus kms tools 03.11.2017 portable [cracksnow]\programs\kmsauto net 2016 v1.5.3 portable |
| %profile%\downloads\kms tools portable 16.11.2017 by ratiborus\programs\kmsauto net 2016 v1.5.3 portable |
| %profile%\downloads\compressed\kmsauto.net.1.5.3.portable\kmsauto.net.1.5.3.portable |
| %temp%\rar$exa0.235\kms tools portable\programs\kmsauto net 2016 v1.5.3 portable |
| %sysdrive%\$recycle.bin\s-1-5-21-2547335818-485395970-549736601-1001 |
| %desktop%\kmsauto net 2016 v1.5.3 portable |
| %sysdrive%\серёжены программы\программное обеспечение\активаторы\kmsauto.net.2016.1.5.3.zip\kmsauto.net.2016.1.5.3 |
| KMSAuto Net.exe |
| $RDJ41CE.exe |
| $RM0BBJ9.exe |
| $RTFP3R8.exe |
| KMSAutoNet_v1.3.5_2018.exe |
| Windows 10 Pro RedStone 3 v1709 Fall Creators Update Activator - nov 2017 -KMSAuto Net.exe |
| $RULGPGT.exe |
| kmsauto net.exe |
| gKMSAuto Net.exe |
| KMSAuto Net 1.5.3.exe |
| KMAutoNet.exe |
| KMSAuto.Net.2016.1.5.3.exe |
| KMSAuto Net 2016 v1.5.3_port.exe |
| KMSAuto Net_Softgozar.com.exe |
| KMSAuto Net v1.5.3.exe |
| KMSAutoNet.exe |
| activator KMS.exe |
| KMSAuto_Net.exe |
| KMSAuto.exe |
| {300E54CE-099E-42E2-853D-7A10053B0FB6} |
| $RT8N4ZU.exe |
| KMSAUTO NET.EXE |
| KMSAuto Net 2016 1.5.3.exe |
| dwh88b4.exe |
| KMSAuto Net.exe.quarantined |
| KMSAutoNet1.5.3.exe |
| KMSAuto_Office.exe |
| KMSAuto |
| $RH36F85.exe |
| $RFKO5KH.exe |
| KMSAuto Net.EXE |
| $RI2083Z.exe |
| $R2G64VB.exe |
|
31.4% |
|
|
13.8% |
|
|
3.9% |
|
|
3.4% |
|
|
2.9% |
|
|
2.7% |
|
|
2.5% |
|
|
2.4% |
|
|
2.3% |
|
|
2.2% |
|
|
1.7% |
|
|
1.6% |
|
|
1.4% |
|
|
1.4% |
|
|
1.3% |
|
|
1.3% |
|
|
1.2% |
|
|
1.2% |
|
|
1.2% |
|
|
1.2% |
|
|
1.0% |
|
|
0.9% |
|
|
0.9% |
|
|
0.8% |
|
|
0.7% |
|
|
0.6% |
|
|
0.6% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.5% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.4% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
| Windows 10 |
72.7% |
|
| Windows 7 |
19.4% |
|
| Windows 8.1 |
6.4% |
|
| Windows Server 2012 R2 |
0.6% |
|
| Windows Server 2008 R2 |
0.3% |
|
| Windows 8 |
0.2% |
|
| Windows XP |
0.2% |
|
| Windows Embedded 8.1 |
0.1% |
|
| Windows Server 2016 |
0.1% |
|
Analysis
| Subsystem: |
Windows GUI |
| PE Type: |
pe |
| OS Bitness: |
32 |
| Image Base: |
0x00400000 |
| Entry Address: |
0x0088760a |
| MVID: |
f216097e-9e12-4f1a-8df7-780a2c80dffb |
| Typelib ID: |
fcaa9736-cfc3-43fa-33da-378396c3a336 |
| Name |
Size of data |
MD5 |
| .text |
8935424 |
d13978447f6ba3d94cdcc36741eb9ddd |
| .rsrc |
48640 |
1776dc784bac737f289591086886274a |
| .reloc |
512 |
1657d5fa19670347348363e60081b643 |