How to remove $R4GRQA5.exe
- File Details
- Overview
- Analysis
$R4GRQA5.exe
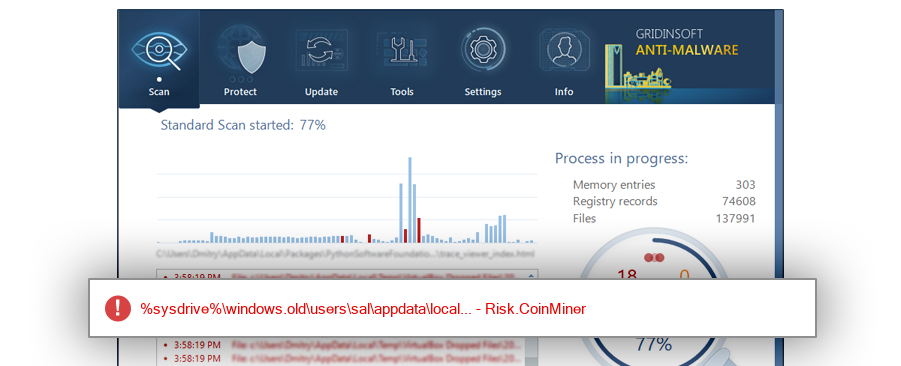
The module $R4GRQA5.exe has been detected as Risk.CoinMiner
File Details
| Product Name: |
|
| Company Name: |
|
| MD5: |
448734529f4689e90624256c8b44c159 |
| Size: |
2 MB |
| First Published: |
2018-03-24 10:06:48 (7 years ago) |
| Latest Published: |
2022-04-03 23:24:37 (3 years ago) |
| Status: |
Risk.CoinMiner (on last analysis) |
|
| Analysis Date: |
2022-04-03 23:24:37 (3 years ago) |
| %temp% |
| %sysdrive%\$recycle.bin |
| %windir% |
| %sysdrive%\$recycle.bin\s-1-5-21-2102602532-1408011781-979871381-1001 |
| %desktop% |
| %sysdrive% |
| %sysdrive%\$recycle.bin\s-1-5-21-2743428373-2065306696-1775936478-1001 |
| %profile%\docume~1 |
| %mydoc% |
| %sysdrive%\temp |
| xmrig.exe |
| $R4GRQA5.exe |
| xmrig.exe.quarantined |
| $R67XS0G.exe |
| $R4ZVRKT.exe |
| $RQD5VTD.exe |
| $RL678FL.exe |
| $RK9GT09.exe |
| $RWAAPK9.exe |
| $RDC0Z0G.exe |
| $RQ3W2F6.exe |
| $R07TIA6.exe |
| $RWZGHNJ.exe |
| $RO0YABI.exe |
| $R420GBG.exe |
| $RWXAJLI.exe |
| $R4DFIOF.exe |
| $R1ZIIIR.exe |
| $RPGIJLV.exe |
| $RCJL45K.exe |
| $RUZMYRV.exe |
| $RKXAWXR.exe |
| $RJ98MMP.exe |
| $R3U3HCT.exe |
| $R0GZL1R.exe |
| $RZG0LTD.exe |
| $RCNP8WL.exe |
| $R52X55N.exe |
| $RK9402X.exe |
| $RQ92ZH0.exe |
| $R9TACO8.exe |
| $R0NESDN.exe |
| $RFLUWEG.exe |
| $R5FFQ65.exe |
| $RIY2K1B.exe |
| $RFH4WGT.exe |
| $R6NSKWN.exe |
| $RU7FZFL.exe |
| $ROME5ZA.exe |
| $RIJMQ7S.exe |
| $RLTCWGT.exe |
| $RCJW1EN.exe |
| $R20354Y.exe |
| $RHHLHV1.exe |
| $R6YEDEX.exe |
| $RHPUC1J.exe |
| $RLGJVA8.exe |
| $RSGUKPX.exe |
| $RP0LEIQ.exe |
| $RLQQHRD.exe |
| $RFMVNPS.exe |
| $RHX5N0V.exe |
| $R8R39CY.exe |
| $RZGA0RC.exe |
| $RTGO87M.exe |
| $RK5IK65.exe |
| $RTEOGTW.exe |
| $RXXJN15.exe |
| $RBS1RME.exe |
| $R8X2397.exe |
| $RPC6XI6.exe |
| $RLDJLAL.exe |
| $R3EW784.exe |
| $R3A2YPD.exe |
| $RYXAZTR.exe |
| $R5FT64C.exe |
| $RD8WIGN.exe |
| $RCOEUQC.exe |
| $RAN69UQ.exe |
| $RAACXZO.exe |
| $R93WDWZ.exe |
| $RHSLKC2.exe |
| $RIWBK9S.exe |
| $RSXSEV0.exe |
| $RZE8VNX.exe |
| $RDHT3GW.exe |
| $R5HDGE9.exe |
| $RUSRPYH.exe |
| $R7ESW5Q.exe |
| $RIP0TD0.exe |
| $RCJQMZM.exe |
| unp236915616.tmp |
| $R6H5XO5.exe |
| $RBF92F8.exe |
| $RRY9HQU.exe |
| $RK7PONK.exe |
| $R0P2QEO.exe |
| $RHEND05.exe |
| $R49EKG2.exe |
| $R2YQ9YS.exe |
| $RAC9RCS.exe |
| $R39OECN.exe |
| $RJB1PO2.exe |
| $RG0QDNB.exe |
| $R0TWX0Y.exe |
| $R36B2ZZ.exe |
| $R4K6ERA.exe |
| $RVGLU3V.exe |
| $RGS1VSJ.exe |
| $R994YX3.exe |
| $RB7666Z.exe |
| $RERR3F8.exe |
| $R90AZEJ.exe |
| $R11REKU.exe |
| $RB7M6NY.exe |
| $RL8Y1R8.exe |
| $RCQPW2B.exe |
| $R0IKBJW.exe |
| unp808655.tmp |
| $RUTZDOG.exe |
| $RGMAJ89.exe |
| $RL2HA8A.exe |
| $RRF91YL.exe |
| $RJM6OHT.exe |
| $RTG7M3X.exe |
| $RPWDBPJ.exe |
| $RH4UGIA.exe |
| 5.exe |
| 6.exe |
| $RCWJT4T.exe |
| $RQ14M49.exe |
| $R1F1T9B.exe |
| $R82BLUE.exe |
| $RBEHG3X.exe |
| xmrig.exe.q_Quarantine_1DE74181_q |
| $R28KGW1.exe |
| $RZMYMNG.exe |
| $RU48HUA.exe |
| $RAVVFVR.exe |
| $R83ELAQ.exe |
| $RPHA312.exe |
| $RDZJH1V.exe |
| $ROOAHN9.exe |
| $RIM3PIP.exe |
| $RK9JFCE.exe |
| $RYMJ778.exe |
| $R9YOS1X.exe |
| $RSNXEZH.exe |
| $R2O8LMP.exe |
| $RLH0VCL.exe |
| $RT120FG.exe |
| XMRIG.del |
| $RWZHHFY.exe |
| $RJVTH9G.exe |
| $RTCJW93.exe |
| $RRXNQPB.exe |
| $RTWJAH8.exe |
| $RGBXV9D.exe |
| $RLL0O2A.exe |
| $R0Q0BNP.exe |
| $RJKZB4I.exe |
| $RI2QIOD.exe |
| $RZPQDM8.exe |
| $RG39K3X.exe |
| xmrig.cu.exe |
| $R521SYD |
| $RXVFXPW.exe |
| $RYF5I4R.exe |
| $RLQS756.exe |
| $R1KBDHJ.exe |
| $RVD7BLZ.exe |
| $RA56NHZ.exe |
| $R9TSTPE.exe |
| $R44PS6T.exe |
| xmrig12.exe |
| $RF1IGCC.exe |
|
28.8% |
|
|
8.6% |
|
|
8.5% |
|
|
6.7% |
|
|
4.9% |
|
|
3.9% |
|
|
3.7% |
|
|
2.8% |
|
|
2.5% |
|
|
2.3% |
|
|
2.0% |
|
|
1.9% |
|
|
1.6% |
|
|
1.5% |
|
|
1.3% |
|
|
1.2% |
|
|
1.2% |
|
|
1.2% |
|
|
1.1% |
|
|
1.1% |
|
|
1.1% |
|
|
1.1% |
|
|
1.0% |
|
|
1.0% |
|
|
0.8% |
|
|
0.7% |
|
|
0.6% |
|
|
0.6% |
|
|
0.6% |
|
|
0.5% |
|
|
0.5% |
|
|
0.4% |
|
|
0.4% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.3% |
|
|
0.2% |
|
|
0.2% |
|
|
0.2% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
|
0.1% |
|
| Windows 10 |
68.7% |
|
| Windows 8.1 |
21.2% |
|
| Windows 7 |
6.0% |
|
| Windows 8 |
3.2% |
|
| Windows Server 2012 R2 |
0.5% |
|
| Windows Server 2012 |
0.3% |
|
| Windows Server 2016 |
0.1% |
|
Analysis
| Subsystem: |
Windows CUI |
| PE Type: |
pe |
| OS Bitness: |
64 |
| Image Base: |
0x0000000000400000 |
| Entry Address: |
0x000014e0 |
| Name |
Size of data |
MD5 |
| .text |
524800 |
0d8d32b7d11cb30aab29987db2f4d318 |
| .data |
1024 |
ee958ae47e957ca1919264713ab9c7dd |
| .rdata |
66048 |
64aad6b35cfdef6b392de95afb972b30 |
| .pdata |
20992 |
2831d6159198f5f7599091989c73a736 |
| .xdata |
19968 |
ff3d0fe2bd123fae88dac8dcfbac6522 |
| .bss |
0 |
00000000000000000000000000000000 |
| .idata |
12288 |
483bc536a61ff17b640049db8a264a6b |
| .CRT |
512 |
d19c3afd7e3e9a9f70fc4950f6696334 |
| .tls |
512 |
bf619eac0cdf3f68d496ea9344137e8b |
| .rsrc |
23040 |
d4b1388c726ae81642a9a0e8acb0ba91 |
| /4 |
3584 |
d3fd521a2cca2d6c93e9fe0434654df1 |
| /19 |
1196544 |
62a9e0fb77106ad6e9579abf2e6f3dd8 |
| /31 |
50688 |
9205208cd917e8865077179edc6344f8 |
| /45 |
75264 |
708317a5ef504f79aca7b7515912036a |
| /57 |
40960 |
0f7c86a8562cc0a850e3f1fad7beb2ec |
| /70 |
18944 |
db6887b7b472486007bd90ee50ab461a |
| /81 |
334848 |
f636133553ebc1a6b48c7d9e22efbbff |
| /92 |
24576 |
44fafc44eabfdf7de9dbe633e4568312 |